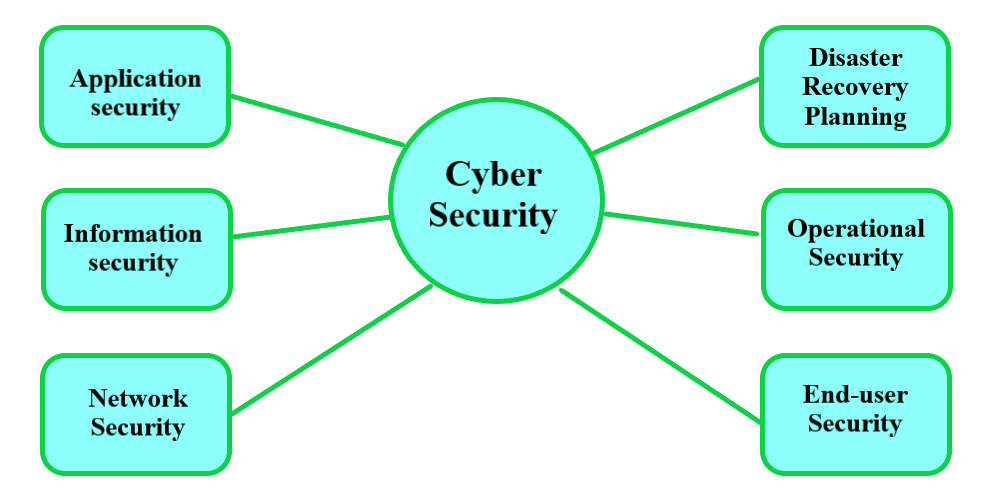
5 Essential Components of Cyber Security
Have you ever wondered how secure your business data really is in this digital era? In a world where cyber threats are constantly evolving, understanding the fundamentals of cyber security is not just a necessity but a critical business strategy. This blog post promises to demystify the concept of cyber security and delve into five key components of cybersecurity.
By the end of this read, you’ll not only grasp the components of cyber security but also learn how to fortify your business against digital threats, especially if you’re operating in the dynamic landscapes of the United States and Canada. Delve into the intricacies of cyber security with this blog, unraveling its five key components of cybersecurity. In today’s dynamic United States and Canada business environments, understanding the elements of cyber security is a necessity.
Wondering how cyber security works? Explore this post to demystify the workings and learn about the critical features of cyber security. For businesses in Toronto, discover local expertise with prominent cybersecurity companies in Toronto. Enhance your security posture with insights into managed cyber security services and strategic cyber security consulting services.
1. Identification and Access Management (IAM)
Identification and Access Management (IAM) stands as the bedrock of effective cybersecurity. It ensures the right individuals have access to resources for the right reasons. This intricate component of cyber security involves robust User Authentication methods, such as passwords, tokens, biometrics, and multi-factor authentication.
Identification and Access Management is the cornerstone components of cyber security, focusing on ensuring that the right individuals have access to the appropriate resources at the right times for the right reasons. In detail:
- User Authentication: This involves verifying the identity of a user before granting access. Methods include passwords, security tokens, biometric verification, and multi-factor authentication.
- Access Control: Once authenticated, users are granted access to resources based on their role and necessity. This is crucial in minimizing the risk of internal threats and data breaches.
- User Lifecycle Management: IAM systems manage the entire user lifecycle, from initial identity verification and role assignment to the eventual revocation of access upon termination of employment or role change.
- Audit and Compliance Reporting: IAM tools provide detailed logs and reports, which are essential for compliance with various data protection regulations and for auditing purposes
Explore IAM and other essential components of cyber security for a holistic defense. For businesses in Toronto, leverage expertise from local cybersecurity companies in Toronto offering managed cyber security services and strategic cyber security consulting services. Understand how cyber security works through these features, fortifying your defense against evolving threats.
2. Threat Protection and Management
Threat Protection and Management is a pivotal components of cybersecurity, employing practices and technologies to shield your business from diverse cyber threats. Explore these key elements of cyber security to fortify your business against evolving cyber threats.
Threat Protection and Management involves a series of practices and technologies designed to protect your business from a myriad of cyber threats. Key aspects include:
- Continuous Monitoring: Implementing tools that continuously monitor your network for unusual activity, which could indicate a breach or an attempted attack.
- Regular Updates and Patch Management: Keeping all software up-to-date to protect against known vulnerabilities.
- Employee Training: Regularly training employees on recognizing and responding to cyber threats, such as phishing attacks.
- Incident Response Planning: Having a well-defined plan for responding to security incidents to minimize damage and recover quickly.
In Toronto, leverage expertise from prominent cybersecurity companies in Toronto offering managed cyber security services and strategic cyber security consulting services to stay ahead of the cybersecurity curve. Understand how cyber security works through these features, ensuring a resilient defense mechanism.
3. Data Protection and Privacy
Data Protection and Privacy form integral components of cybersecurity, ensuring the secure handling of sensitive information and compliance with privacy laws. Explore these essential elements of cyber security to fortify your business against evolving cyber threats.

Data Protection and Privacy are about safeguarding sensitive information from unauthorized access and ensuring compliance with privacy laws. This includes:
- Encryption: Encrypting data both at rest and in transit to ensure that even if data is intercepted or accessed, it remains unreadable.
- Data Masking: Using methods to hide sensitive data, ensuring that it’s only accessible to authorized personnel.
- Data Rights Management: Implementing policies and technologies that control who can access and what they can do with the data.
- Compliance with Regulations: Ensuring adherence to data protection laws like GDPR, HIPAA, etc., which is crucial for businesses operating internationally or handling sensitive information.
For businesses in Toronto, tap into the expertise of leading cybersecurity companies in Toronto, providing comprehensive managed cyber security services and strategic cyber security consulting services. Understand how cyber security works through these features, safeguarding your data and privacy effectively.
4. Network Security
Network Security is a cornerstone among the components of cyber security, dedicated to preserving the usability and integrity of your network and data. Explore these critical aspects to fortify your business against evolving cyber threats.
Network Security focuses on protecting the usability and integrity of your network and data. It includes:
- Firewalls: Establishing barriers between trusted and untrusted networks to control incoming and outgoing network traffic based on an applied rule set.
- Intrusion Detection and Prevention Systems (IDPS): Tools that monitor network traffic for suspicious activity and react to detected threats.
- Virtual Private Networks (VPNs): Creating a secure and encrypted connection over a less secure network, such as the internet.
- Regular Security Assessments: Conducting vulnerability scans and penetration testing to identify and address security weaknesses.
For businesses in Toronto, consider leveraging the expertise of renowned cybersecurity companies in Toronto offering comprehensive managed cyber security services and strategic cyber security consulting services. Understand how the features of cyber security work collectively to safeguard your network and data.
5. Disaster Recovery and Business Continuity
Disaster Recovery and Business Continuity form integral components of cyber security, ensuring business resilience in the face of major incidents or disasters. Thoroughly devised Disaster Recovery Plans are critical, offering detailed strategies for swiftly restoring hardware, applications, and essential data post-disaster.

Disaster Recovery and Business Continuity planning is about ensuring your business can continue to operate in the event of a major incident or disaster. This involves:
- Disaster Recovery Plans: Detailed strategies for quickly restoring hardware, applications, and data critical to business operations after a disaster.
- Business Continuity Plans: Broader strategies that ensure the maintenance of essential functions during and after a disaster, including temporary relocation, remote work options, and maintaining critical supply chains.
- Regular Testing and Updates: Regularly testing and updating recovery plans to ensure they are effective and current with the business’s evolving needs.
- Data Backup Solutions: Implementing robust data backup solutions, including off-site or cloud backups, to ensure data can be recovered in the event of loss or corruption.
For businesses in Toronto, consider the expertise of leading cybersecurity companies in Toronto, offering comprehensive managed cyber security services and strategic cyber security consulting services. Explore how the various features of cyber security work collaboratively, safeguarding your business against potential disruptions.
Conclusion
Understanding and implementing these five components of cybersecurity is crucial for small and medium businesses in the United States and Canada. In today’s digital age, where cyber threats are a constant concern, taking proactive steps to secure your business’s digital assets is not just advisable; it’s essential. By focusing on these components of cyber security, you can establish a robust defense against the myriad digital threats facing businesses today.

Grasping and putting into action the essential components of cyber security is crucial for the endurance of small and medium-sized enterprises. By focusing on these elements of cyber security, you can create a robust defense against the myriad of digital threats facing businesses today. If you’re looking to enhance your business’s cyber security posture, consider partnering with GoGeekz. Our expertise in managed cyber security services and cyber security consulting can help safeguard your business against digital threats, ensuring peace of mind and continued success. Contact GoGeekz today to learn how we can fortify your cyber defenses and keep your business secure in the digital world.
Our specialized expertise in managed cyber security services and cyber security consulting services ensures peace of mind and sustained success. Contact GoGeekz today to discover how we can fortify your cyber defenses and maintain the security of your business in the digital world. Explore what sets apart the various features of cyber security and how they collectively work to safeguard your business against potential threats.
FAQs
Industry Experiences
Innovative services for your business
We’re dedicated to making your businesses reliable, efficient, and safe.
We’re a one-stop solution for everything IT you need. Whatever you need, we got you covered:
Identification and Access Management (IAM) refers to the processes and technologies used to manage and verify the identities of users accessing an organization’s systems and networks.
It includes tools for authentication, authorization, user lifecycle management, and compliance reporting. IAM is crucial for ensuring that only authorized individuals have access to sensitive data and systems. Enhance your business’s security with GoGeekz!
Threat Protection and Management services provide businesses with the necessary tools and expertise to identify, analyze, and respond to cyber threats. These services include continuous monitoring of networks for suspicious activities, regular software updates, employee training on cyber threat awareness, and incident response planning.
They are essential in safeguarding businesses from evolving cyber threats. Elevate your cybersecurity defenses—partner with GoGeekz for robust protection against evolving threats and secure your business with confidence!
Data Protection and Privacy are vital for businesses to maintain the confidentiality and integrity of sensitive information. This involves implementing measures like encryption, data masking, and rights management.
It also includes compliance with data protection regulations. Protecting data not only safeguards against breaches but also builds trust with customers and partners.
Protect your business’s sensitive information with GoGeekz! Our Data Protection and Privacy services employ cutting-edge measures like encryption, data masking, and rights management.
Key elements of Network Security include firewalls, intrusion detection and prevention systems, virtual private networks (VPNs), and regular security assessments.
These elements work together to protect a business’s network from unauthorized access, misuse, or threats, ensuring the integrity and usability of both the network and the data it carries. Secure your business’s network with GoGeekz! Our Network Security services encompass firewalls, intrusion detection and prevention systems, VPNs, and regular security assessments.
Disaster Recovery plans focus on the restoration of IT infrastructure and data access after a disaster, aiming to minimize downtime and data loss. Business Continuity plans, on the other hand, are broader and ensure that critical business functions continue during and after a disaster. This may include strategies like remote work, maintaining critical supply chains, and temporary relocation. Contact us today for comprehensive planning, including strategies like remote work and supply chain management. Regular testing and updates guarantee your readiness for unforeseen events.