But imagine if you keep your keys in a safe that can only be accessed with a constantly changing security code, which can only be obtained through a secure phone app that requires your fingerprint or face recognition, you have employed Multi Factor Authentication (MFA) tools to enhance the security of your valuables.
This analogy mirrors the importance of MFA in the digital realm, especially for businesses. Implementing an authentication system for small business or adopting enterprise MFA solutions acts as a virtual safe, significantly reducing the risk of unauthorized access and the potential repercussions of not having MFA in place.
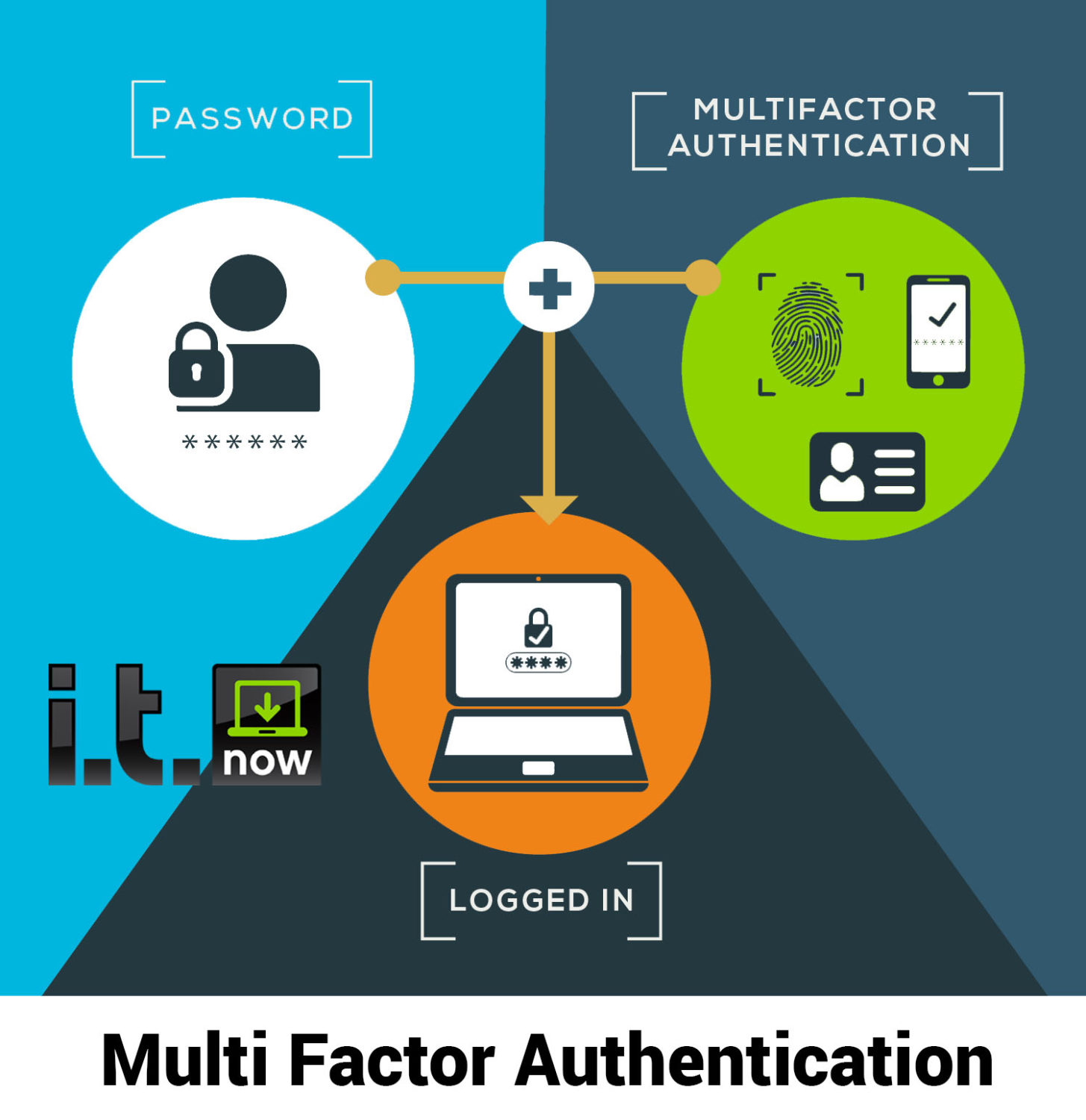
In the context of cybersecurity, the analogy extends to the question of “how effective is multi-factor authentication?” The answer lies in its ability to create multiple layers of defense against cyber threats, making it exponentially more challenging for criminals to gain access to sensitive information. The ongoing evolution of cyber threats emphasizes the need for robust authentication cybersecurity measures, and MFA stands as a frontline defense in this digital battleground.
Read more: improve endpoint security tips
What is Multi Factor Authentication?
What is multi factor authentication (MFA)? At its core, MFA is a cybersecurity strategy that adds an extra layer of protection by requiring users to provide multiple forms of identification before accessing a system or account. For small businesses, implementing an authentication system for small business is a pragmatic step in bolstering security measures.
The risk of not having MFA is particularly significant for smaller enterprises, as cybercriminals often target them due to perceived vulnerabilities. By adopting user-friendly multi factor authentication tools, small businesses can fortify their cybersecurity defenses and deter potential unauthorized access attempts.
You’ll recognize the MFA process if you use online banking. It’s become the standard way to make it harder for criminals to access important data, like your financial or personal medical information. Despite the effectiveness of MFA, many businesses still rely on simple usernames and passwords, which offer minimal protection against cyber-attacks.
Despite the effectiveness of MFA, many businesses still rely on simple usernames and passwords, inadvertently exposing themselves to the significant risk of not having MFA in place. Implementing an authentication system for small business can be a transformative step in fortifying digital defenses.
However, with user-friendly multi factor authentication tools, small businesses can elevate their cybersecurity posture and thwart potential cyber-attacks. For larger enterprises, adopting comprehensive enterprise MFA solutions is not just an option; it’s a strategic imperative in safeguarding vast repositories of sensitive data.
Read more: small business managed it solutions
How Effective is Multi Factor Authentication?
The question of “how effective is multi factor authentication?” gains relevance as businesses reassess their cybersecurity strategies. The answer lies in recognizing MFA as a dynamic and adaptive shield against evolving cyber threats.
The effectiveness of multi factor authentication is indisputable in today’s cybersecurity landscape. As cyber threats become more sophisticated, traditional authentication methods, with just usernames and passwords, fall short in providing robust protection. Multi factor authentication introduces an additional layer of security by incorporating multiple forms of identification, such as biometrics, smart cards, or one-time codes.
The risk of not having MFA becomes apparent when considering the relentless tactics employed by cybercriminals. User-friendly multi factor authentication tools empower small enterprises to enhance their security posture, reducing the likelihood of falling victim to cyber-attacks.
The urgency to prioritize authentication cybersecurity has never been more apparent. It’s time for businesses of all sizes to transition from the standard to enhanced authentication measures, embracing the security offered by advanced multi factor authentication tools and fortifying their defenses against the ever-present risk of cyber threats.
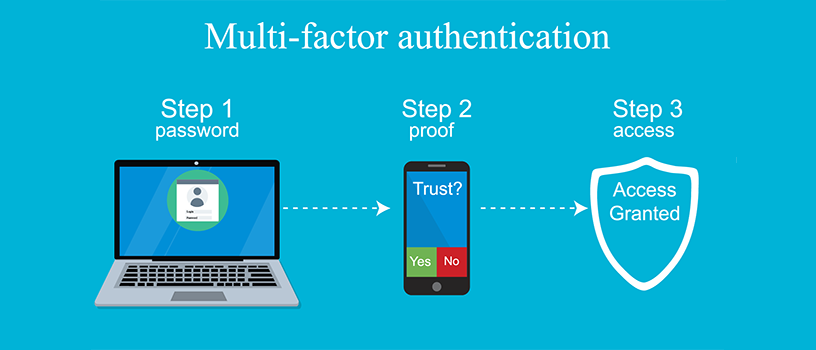
How Does Multi Factor Authentication Work?
Curious about how multi-factor authentication (MFA) works? This robust security mechanism operates on the principle of requiring users to provide multiple forms of identification before accessing a system or account. The primary goal is to add layers of defense beyond conventional usernames and passwords, mitigating the risk of not having MFA in place.
IT specialist Dave from GoGeekz urges businesses to upgrade to MFA to safeguard their data, including customers’ personal information, from cyber criminals who are becoming more sophisticated in their methods.
Most of us now use MFA to log in to our banking apps and many of our personal online accounts. So it’s surprising how little security businesses are using to keep their data safe. That data often includes customers’ private, personal information. If that fell into the wrong hands, the consequences could be disastrous. The frightening fact is that most small companies that suffer a serious cyber attack don’t survive. The cost of recovery, and the damage to their reputation, is just too great.
Dave added: “Cyber attacks are getting more and more sophisticated, and business owners could be risking everything if they don’t make the simple step up to MFA. We do this kind of work every day, so we know that for most companies Multi-Factor Authentication isn’t difficult to implement. But the security benefits are huge – that’s why we recommend that all businesses should upgrade to MFA right away.”
Read more: cloud computing solutions for business
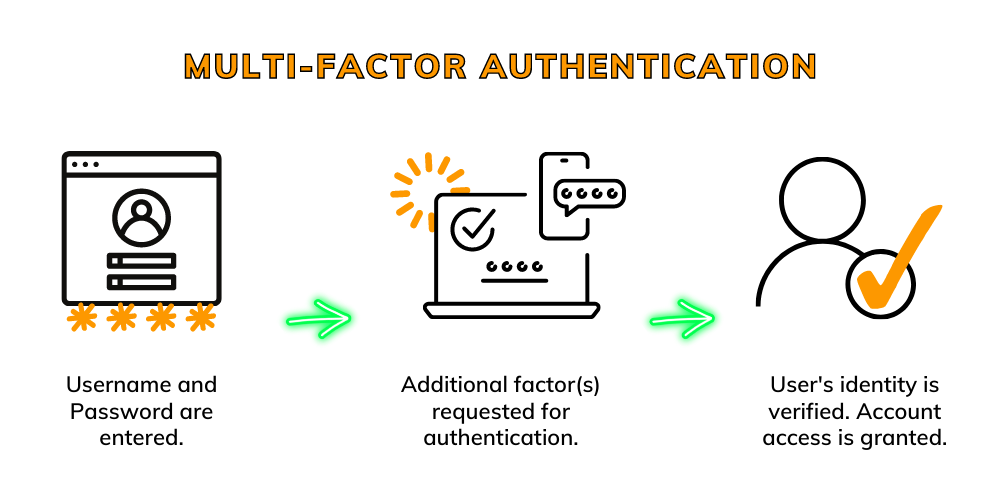
How to Implement Multi Factor Authentication?
Wondering how to implement multi factor authentication (MFA) effectively? The process involves several key steps to ensure a seamless integration that fortifies your authentication cybersecurity measures.
- Evaluate Your Needs: Begin by assessing your organization’s requirements. Understand the nature of your data, the sensitivity of information, and the potential risks. This evaluation will guide the selection of appropriate multi factor authentication tools.
- Choose the Right Tools: Selecting the right MFA tools is pivotal. For a small business authentication system, opt for user-friendly tools that align with the scale and needs of your enterprise. Larger organizations may explore comprehensive enterprise MFA solutions that integrate seamlessly with existing systems.
- Training and Communication: Effective implementation involves educating your staff on the new authentication system. Clearly communicate the benefits and necessity of MFA, emphasizing the risk of not having MFA in place.
- Test and Refine: Conduct thorough testing before fully deploying MFA. Identify any potential issues and refine the implementation based on user feedback. This iterative process ensures a smooth transition and addresses any unforeseen challenges.
- Monitor and Update: Continuous monitoring is key to maintaining a robust security posture. Regularly update MFA tools and protocols to stay ahead of evolving cyber threats.

By navigating these steps, businesses can implement multi factor authentication successfully, enhancing their cybersecurity defenses and mitigating the risks associated with outdated authentication methods.
Read more: search engines optimization techniques






