| Table of Contents |
|---|
| Use an endpoint protection service |
| Educate your users |
| FAQs |
| Monitor your endpoints |
| Protect your API Endpoints |
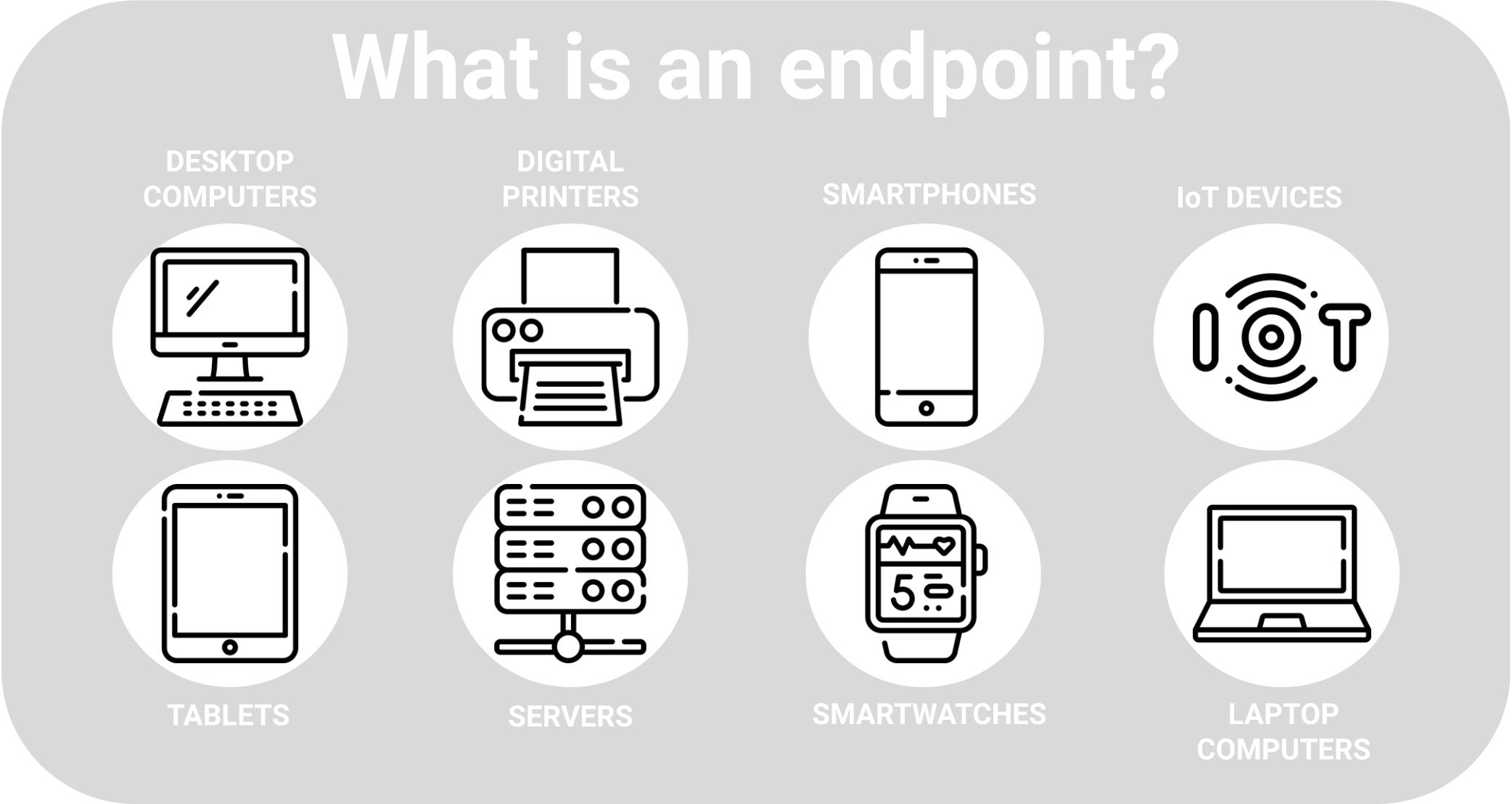
Endpoint protection is a term that refers to the security measures taken to protect devices such as laptops, smartphones, tablets and servers from cyberattacks. These devices are called endpoints because they are the points of entry for hackers to access a network or system.
Implementing an endpoint protection platform involves using advanced endpoint security tools and managed endpoint protection to safeguard against data breaches, malware, and ransomware. Regular monitoring, updates, and improvements are essential for effective endpoint security management, ensuring your defense stays resilient in the ever-evolving cyber landscape. A robust endpoint protector is crucial for maintaining the confidentiality, integrity, and availability of your data and systems.
Endpoint security can prevent data breaches, malware infections, ransomware attacks and other threats that can compromise the confidentiality, integrity and availability of your data and systems. However, endpoint protection is not a one-time solution. It requires constant monitoring, updating and improvement to keep up with the evolving cyber landscape.
Read more: small business managed it solutions
What is Endpoint Protection?
Endpoint protection is a pivotal aspect of modern cybersecurity. It involves securing individual devices, or endpoints, such as computers, smartphones, and servers, against cyber threats. An effective endpoint protection platform incorporates various security measures, including antivirus, firewalls, and encryption, to ensure comprehensive defense. The role of an endpoint protector is to safeguard these entry points from malware, ransomware, and unauthorized access.
Utilizing advanced endpoint security tools and adopting best practices, such as regular updates and user education, enhances the overall endpoint security protection. With the increasing sophistication of cyber threats, having a well-managed endpoint security management strategy is essential for businesses to navigate the evolving digital landscape securely
Understanding what is endpoint protection is becomes essential in today’s cyber landscape, where a well-managed strategy is paramount for safeguarding against evolving threats.
Endpoint Protection Tips to achieve better Security for your Network
Endpoint protection is paramount in safeguarding your devices and network against cyber threats. To bolster your defense, consider implementing a robust endpoint protection platform and utilizing cutting-edge endpoint security tools. A reliable endpoint protector is essential for preventing data breaches and ensuring the overall security of your systems. Explore the benefits of managed endpoint protection and managed endpoint security services to enhance your cybersecurity strategy.
Additionally, understanding the nuances of endpoint security management is key to fortifying your defense against evolving cyber risks. With these tips, you can elevate your overall endpoint security protection for a more resilient and secure digital environment. In this post, we will share some simple tips on how to achieve better endpoint security for your devices and network.
Read more: search engines optimization techniques
1. Use an Endpoint Protection Service
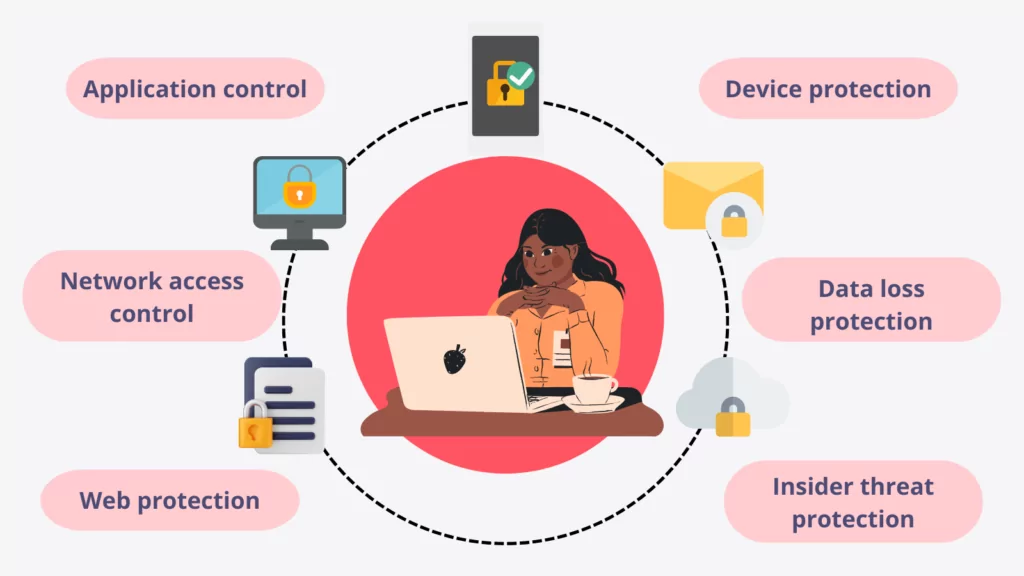
An endpoint protection service is a software solution that provides comprehensive security for your endpoints. It can include features such as antivirus, firewall, anti-malware, anti-ransomware, device encryption, data backup and recovery, remote wipe and lock, patch management and more.
An endpoint protection service can help you automate the security tasks for your endpoints and reduce the workload for your IT staff. It can also provide centralized management and visibility of your endpoints’ status and activity. Moreover, an endpoint protection service can offer cloud-based or hybrid deployment options that can scale with your business needs.
Some examples of endpoint protection services are Bitdefender Gravity Zone Business Security, Kaspersky Endpoint Security Cloud Plus and McAfee Endpoint Security. By automating security tasks, an endpoint protection platform not only enhances security but also alleviates the workload for your IT staff.
2. Educate your Users
One of the biggest challenges in endpoint protection is human error. Users may unknowingly click on malicious links or attachments in phishing emails or visit compromised websites that can infect their devices with malware or ransomware.
Therefore, educating your users on how to recognize and avoid common cyber threats such as phishing emails or fake pop-ups is important. You should also establish clear policies and guidelines on using your devices securely, such as using strong passwords or biometric authentication methods; enabling multi-factor authentication; avoiding public Wi-Fi networks or VPNs; updating software regularly; backing up data frequently; reporting any suspicious activity or incidents; etc.
You should also conduct regular training sessions and simulations to test your users’ awareness and readiness against cyberattacks. Regular training sessions and simulations enhance users’ awareness and preparedness against cyberattacks, ensuring a proactive defense. Implementing these measures not only strengthens endpoint security protection but also cultivates a security-conscious culture within your organization.
Read More: BEC in cyber security
3. Monitor your Endpoints
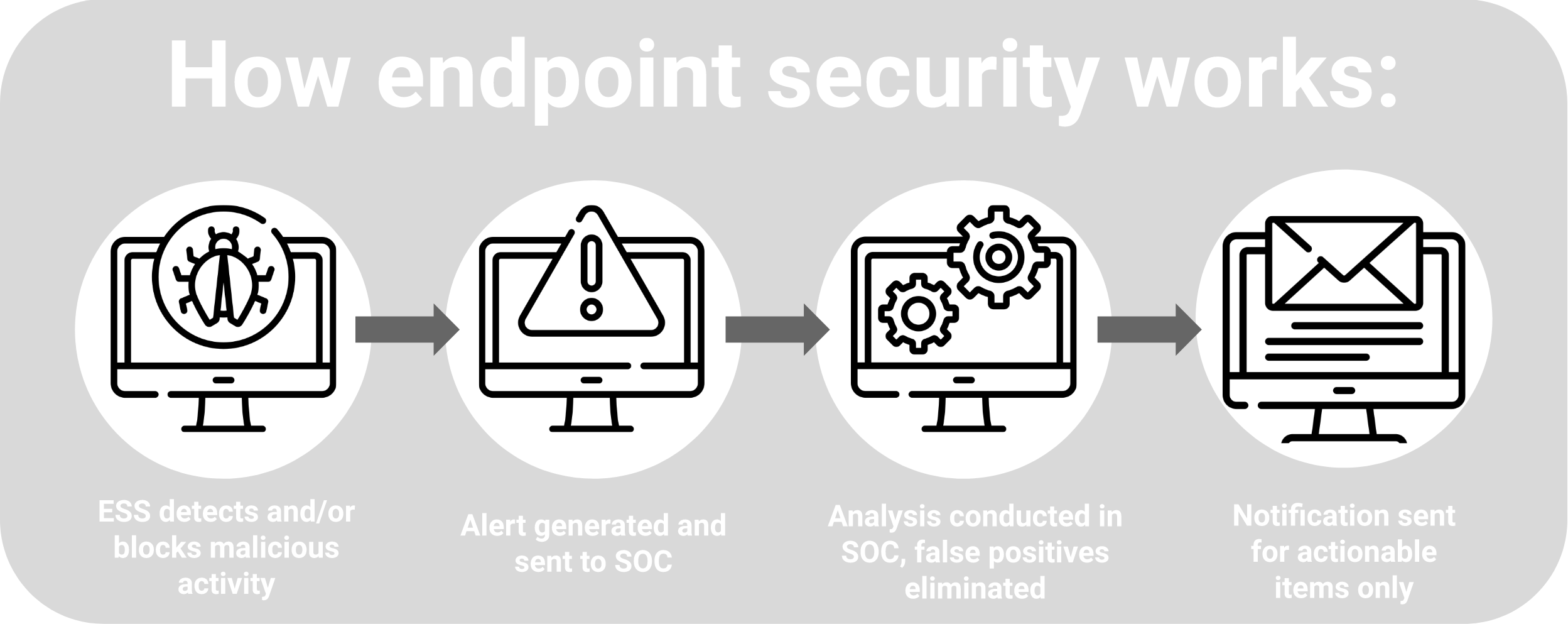
Another key aspect of endpoint protection is monitoring your endpoints’ performance and behavior. You should be able to detect any anomalies or signs of compromise such as unusual network traffic; high CPU usage; unauthorized file changes; new or unknown processes; etc.
You should also be able to respond quickly and effectively to any incidents by isolating infected devices; removing malware or ransomware; restoring data from backups; notifying relevant stakeholders; etc. Leveraging tools like endpoint detection and response (EDR) solutions or security information and event management (SIEM) solutions enhances your ability to monitor endpoint activity and receive alerts for potential threats.
You can use tools such as endpoint detection and response (EDR) solutions or security information and event management (SIEM) solutions to help you monitor your endpoints’ activity and alert you of any potential threats.
Some examples of EDR solutions are CrowdStrike Falcon Insight, SentinelOne, ActiveEDR and Sophos Intercept X Advanced with EDR.
Some examples of SIEM solutions are Splunk Enterprise Security (ES), IBM QRadar SIEM and LogRhythm NextGen SIEM Platform.
Read More: Signs of malware on your computer
4. Protect your API Endpoints
API endpoints are interfaces that allow communication between different applications or systems over the internet. They can enable features such as data sharing; integration; automation; etc.
However, API endpoints can also expose sensitive information or functionality that can be exploited by hackers if they are not properly secured.
For example, hackers may try to access unauthorized data by manipulating API parameters;
Inject malicious code by exploiting API vulnerabilities;
or launch denial-of-service attacks by overwhelming API servers with requests;
Therefore, you should protect your API endpoints by implementing best practices such as using HTTPS protocol; validating input and output; encrypting data in transit and at rest; implementing authentication and authorization mechanisms; limiting request rate and size; monitoring API usage and performance;etc.
You should also use tools such as API security testing tools or API management platforms to help you test, manage, and secure your API endpoints.

Some examples of API security testing tools are OWASP ZAP, Postman, and SoapUI. Some examples of API management platforms are Apigee, MuleSoft Anypoint Platform, and AWS API Gateway. Additionally, tools like API security testing tools (e.g., OWASP ZAP, Postman, SoapUI) and API management platforms (e.g., Apigee, MuleSoft Anypoint Platform, AWS API Gateway) play a crucial role in testing, managing, and securing API endpoints. Ensuring the protection of these crucial interfaces complements overall endpoint security management, contributing to a robust cybersecurity strategy for your business.
Endpoint protection is a vital component of cybersecurity that can help you safeguard your devices, data, and systems from cyberattacks. By following these simple endpoint protection tips, you can achieve better endpoint security for your business.
FAQs:
Industry Experiences
Innovative services for your business
We’re dedicated to making your businesses reliable, efficient, and safe.
We’re a one-stop solution for everything IT you need. Whatever you need, we got you covered:
Endpoint protection is a term that refers to the security measures taken to protect devices such as laptops, smartphones, tablets and servers from cyberattacks.
These devices are called endpoints because they are the points of entry for hackers to access a network or system. GoGeekz – Guard your endpoints, safeguard your business!
An endpoint protection platform is a software solution that provides comprehensive security for your endpoints.
It can include features such as antivirus, firewall, anti-malware, anti-ransomware, device encryption, data backup and recovery, remote wipe and lock, patch management and more. Let’s secure your devices and fortify your defenses. Your business resilience starts here!
API endpoints are interfaces that allow communication between different applications or systems over the internet. They can enable features such as data sharing; integration; automation; etc. However, API endpoints can also expose sensitive information or functionality that can be exploited by hackers if they are not properly secured.
Therefore, you should protect your API endpoints by implementing best practices such as using HTTPS protocol; validating input and output; encrypting data in transit and at rest; implementing authentication and authorization mechanisms; limiting request rate and size; monitoring API usage and performance; etc.
Endpoint protection can face various challenges such as the increasing number and diversity of endpoints; the growing sophistication and frequency of cyberattacks; the lack of user awareness and compliance; the shortage of skilled security professionals; the difficulty of integrating different security solutions; etc.
Take control of your cybersecurity with GoGeekz! Overcome challenges in endpoint protection – secure diverse endpoints, combat cyber threats, boost user awareness. Act now for a resilient defense! Contact us today.
If you are looking to learn more about endpoint protection, feel free to contact our agents at GoGeekz where we can provide you the best service!