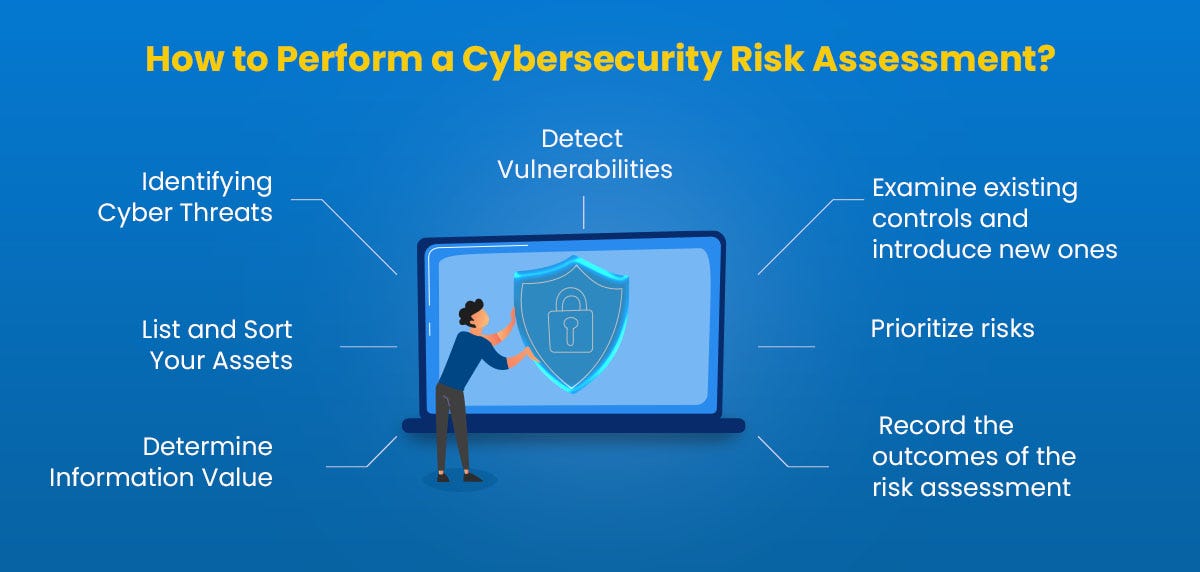
Perform Cybersecurity Risk Assessment in 5 Simple Steps
Are you constantly worried that your business might be the next victim of a cyberattack? In an era where digital threats are evolving at an unprecedented pace, ensuring the security of your IT infrastructure is not just a necessity but a critical survival strategy. For small and medium businesses in Canada and the United States, understanding and mitigating cyber risks can mean the difference between thriving and being sidelined.

As you progress, integrate effective risk management in cyber security strategies to proactively address emerging threats. Understand the intricate dynamics of the threat risk vulnerability matrix, and establish a robust risk assessment framework tailored to your business needs.
This blog post promises to demystify the process of cybersecurity risk assessment, offering you a straightforward roadmap to safeguard your assets. By the end, you’ll be equipped with the knowledge to fortify your defenses and steer your business toward a more secure future.
What Companies Should Perform a Cybersecurity Risk Assessment?
Every business that interacts with digital technology, which is virtually all in today’s market, needs to conduct regular cybersecurity risk assessments. This is particularly crucial for small and medium-sized enterprises (SMEs) that might not have the robust IT departments of larger corporations but face the same level of threats. Implementing effective risk management in cyber security is paramount to safeguard against the ever-evolving landscape of cyber threats.
Conducting an IT risk assessment and a comprehensive network security assessment ensures a thorough understanding of the threat risk vulnerability matrix. Having a well-defined risk assessment framework and leveraging professional risk assessment services enhances the overall security posture of a business.
Read More: Benefits of managed services model
Benefits of Performing a Security Risk Assessment
Embracing effective risk management in cyber security not only mitigates vulnerabilities but also fosters a proactive approach to emerging threats. Conducting a meticulous IT risk assessment enables businesses to identify and address potential weaknesses in their technological infrastructure.
Simultaneously, a strategic network security assessment scrutinizes the broader digital landscape, ensuring a comprehensive defense mechanism. By understanding the threat risk vulnerability matrix, organizations can tailor a robust risk assessment framework tailored to their unique needs. Furthermore, professional risk assessment services provide expert guidance, equipping businesses to proactively navigate the ever-evolving cybersecurity landscape.
![]() Proactive Threat Identification: Understand the specific threats and vulnerabilities facing your business, allowing for proactive remediation.
Proactive Threat Identification: Understand the specific threats and vulnerabilities facing your business, allowing for proactive remediation.
![]() Compliance and Regulatory Assurance: Ensure your business meets industry standards and regulatory requirements, avoiding potential fines and legal issues.
Compliance and Regulatory Assurance: Ensure your business meets industry standards and regulatory requirements, avoiding potential fines and legal issues.
![]() Resource Optimization: Allocate your cybersecurity budget more effectively by focusing on high-priority risks.
Resource Optimization: Allocate your cybersecurity budget more effectively by focusing on high-priority risks.
![]() Stakeholder Confidence: Build trust with customers, investors, and partners by demonstrating a commitment to cybersecurity.
Stakeholder Confidence: Build trust with customers, investors, and partners by demonstrating a commitment to cybersecurity.
Perform Cybersecurity Risk Assessment in 5 Simple Steps
Step 1: Identify Your Assets
The cornerstone of a robust cybersecurity risk assessment framework is a clear understanding of the assets within your organization. Assets are essentially anything of value to your company that relies on digital or network connectivity. This includes tangible assets like servers, computers, and networking equipment, as well as intangible assets such as software applications, stored data (customer information, intellectual property), and even your company’s reputation.
Use Case:
An accounting firm in the US holds sensitive tax records and financial statements for its clients. Identifying and cataloging these digital assets, along with the systems that process and store them, is essential for understanding what needs protection.
Pro Tip:
Don’t overlook less obvious assets such as digital certificates and intellectual property. The more comprehensive your asset inventory, the more effective your cybersecurity risk assessment will be.
Step 2: Pinpoint Potential Threats
With a clear inventory of your assets, the next step is to identify the myriad of threats that could compromise them. Threats can range from external attacks like phishing, malware, and ransomware, to internal risks such as disgruntled employees or accidental data breaches. Understanding the threat landscape is crucial for preparing defenses that are as dynamic as the threats themselves.
Use Case:
A law firm in Canada might face threats from cybercriminals looking to steal sensitive litigation information or personal data of clients, which could be used for identity theft or sold on the dark web.
Pro Tip:
Leverage threat intelligence platforms and stay abreast of the latest cyber threat reports to understand emerging threats and adapt your risk assessment framework accordingly.
Check out our other blog: Why IT Support 24/7 is Essential
Step 3: Identify Vulnerabilities
Vulnerabilities are the weaknesses in your system that could be exploited by threats to gain unauthorized access or cause harm. This step involves conducting vulnerability scans, penetration testing, and security assessments to uncover flaws in your network security, software, and other critical systems.
Use Case:
An architectural firm using outdated project management software might be vulnerable to exploits that could lead to unauthorized access to detailed building plans and client information.
Pro Tip:
Regularly scheduled vulnerability assessments and embracing a policy of continuous monitoring can help catch new vulnerabilities as they arise, keeping your risk assessment framework up to date.
Step 4: Analyze and Prioritize Risks
Risk analysis involves evaluating the potential impact of identified threats exploiting your vulnerabilities and determining the likelihood of such events. This step helps in prioritizing risks based on their potential impact on your business, allowing you to allocate resources more effectively.
Use Case:
An immigration firm might determine that a data breach revealing client immigration status or personal details would not only have legal ramifications but also severely damage the firm’s reputation, making it a high-priority risk.
Pro Tip:
Utilize a risk assessment framework to systematically evaluate and prioritize risks. This can help in making informed decisions about where to focus your cybersecurity efforts.
Read More: Top 10 Managed Antivirus Software
Step 5: Implement Mitigation Strategies
The final step is all about taking action to address the identified risks. This could involve implementing new security measures, enhancing existing controls, or even accepting certain risks if they fall within your risk appetite. The goal is to reduce vulnerabilities, deter threats, and minimize the impact of any potential security incidents.
Use Case:
To protect against data breaches, an accountant firm might implement multi-factor authentication for all client accounts, encrypt client data both at rest and in transit, and conduct regular cybersecurity awareness sessions for its staff.
Pro Tip:
Risk mitigation is an ongoing process. Regularly review and update your cybersecurity measures in response to new threats, vulnerabilities, and business changes.
Check out our other blog: Phishing Prevention and Email Safety
What Problems Does a Security Risk Assessment Solve?
A cybersecurity risk assessment plays a crucial role in identifying and mitigating potential threats in the digital landscape. When it comes to cyber risk, organizations must prioritize effective risk management in cyber security to safeguard their sensitive information.
An integral aspect of this process is conducting regular it risk assessments and network security assessments. By employing a comprehensive threat risk vulnerability analysis, businesses can proactively address vulnerabilities and fortify their defenses. Establishing a robust risk assessment framework becomes paramount, guiding the implementation of protective measures.
Embracing professional risk assessment services further enhances an organization’s resilience against evolving threats in the dynamic cyber landscape. Integrating these strategies ensures a proactive stance against potential vulnerabilities and reinforces the overall cybersecurity posture.
Check out our other blog: What is Unified Threat Management?
 Vulnerability Detection: The Digital Diagnostic
Vulnerability Detection: The Digital Diagnostic
Imagine your network as a living, breathing organism. Just as a physician conducts a thorough examination to keep you in top health, a cybersecurity risk assessment performs a critical diagnostic of your network. It meticulously reviews your hardware, software, and network configurations, identifying and documenting the vulnerabilities that could potentially serve as gateways for cyber risk attackers. This stage of IT risk assessment is foundational, highlighting the areas that need immediate intervention to shield your digital assets from unauthorized access and potential breaches.
 Threat Intelligence: Understanding Your Digital Adversaries
Threat Intelligence: Understanding Your Digital Adversaries
In the vast ecosystem of the internet, threats like ransomware, phishing, and APTs (advanced persistent threats) lurk in the shadows, ready to strike. Conducting a security risk assessment framework is akin to developing a deep understanding of the predators in the wild. It’s about gaining actionable intelligence on the varied threats that your business may encounter. With a network security assessment, you become adept at recognizing these threats, allowing you to adapt and fortify your defenses effectively and resiliently against the unique challenges your company faces.
 Risk Prioritization: Strategic Cyber Defense
Risk Prioritization: Strategic Cyber Defense
Not every cyber risk warrants a red alert. The art of risk management in cyber security involves discerning which risks could turn into full-blown catastrophes and which are mere nuisances. Through a risk assessment framework, businesses can prioritize risks based on their potential impact, ensuring that the lion’s share of attention and resources is dedicated to fortifying against the most destructive threats. This critical prioritization is essential for efficient resource allocation, aligning your cybersecurity initiatives with your broader business objectives.
Check out our other blog: What is Disaster Recovery?
 Customized Defense Strategies: Your Unique Cybersecurity Blueprint
Customized Defense Strategies: Your Unique Cybersecurity Blueprint
When it comes to cybersecurity, there’s no universal solution. A security risk assessment framework lays the groundwork for a bespoke it risk management in cyber security strategy that complements your business’s specific needs and objectives. Whether it involves deploying cutting-edge encryption, ramping up employee cybersecurity training, or implementing robust multi-factor authentication, the strategies developed post-assessment are custom-fitted to your business’s operational framework. This personalized approach ensures that your cyber risk defenses are as unique as your business.

 Regulatory Compliance: Navigating the Legal Cyber Maze
Regulatory Compliance: Navigating the Legal Cyber Maze
The modern business landscape is not just about innovation and growth—it’s also about compliance. With data protection and privacy laws like GDPR, HIPAA, and CCPA becoming more stringent, a cybersecurity risk assessment becomes indispensable. It aids in identifying any compliance gaps and provides a proactive plan to address them, helping you to steer clear of severe financial and legal repercussions. It’s a crucial step in safeguarding not just your data but also your company’s reputation and trustworthiness.
Check out our other blog: 9 Best Microsoft Office 365 Features
Conclusion
In conclusion, conducting a robust cybersecurity risk assessment is not just a preemptive measure but a strategic imperative for safeguarding your business against evolving threats. Recognizing the significance of cyber risk, organizations must integrate effective risk management in cyber security into their operational fabric. Implementing regular it risk assessments and network security assessments becomes a cornerstone in fortifying digital defenses.
Establishing a resilient risk assessment framework is the foundation for informed decision-making, guiding resource allocation. Embracing professional risk assessment services ensures a comprehensive defense strategy, preparing businesses to navigate the intricate landscape of cyber threats successfully.
Performing a cybersecurity risk assessment is an essential step in protecting your business from digital threats. By following these five simple steps, small and medium businesses can develop a clear understanding of their cybersecurity posture, prioritize their efforts, and allocate resources effectively. Remember, in the realm of cybersecurity, knowledge is not just power—it’s protection.
Don’t wait for a breach to happen before taking action. Start your cybersecurity journey today and ensure your business is equipped to face the digital challenges of tomorrow.
FAQs
Industry Experiences
Innovative services for your business
We’re dedicated to making your businesses reliable, efficient, and safe.
We’re a one-stop solution for everything IT you need. Whatever you need, we got you covered:
A cybersecurity risk assessment is a critical evaluation process that identifies and analyzes potential cyber risks that could compromise your IT infrastructure.
It’s a strategic approach to uncovering vulnerabilities, assessing network security, and determining the potential impact of threats on your business. GoGeekz specializes in providing comprehensive risk assessment services to protect your digital assets.
Cyber risk encompasses any threat that could exploit vulnerabilities in your systems and networks, leading to data breaches, financial loss, and damage to your reputation.
Effective risk management in cybersecurity means having a solid plan to prevent, detect, and respond to these threats. GoGeekz can help you create a robust defense strategy tailored to your business.
IT risk assessment is a component of a broader cybersecurity risk assessment focusing specifically on information technology.
It involves evaluating the risks associated with your IT systems, software, and data, and putting in place measures to mitigate these risks. With GoGeekz, gain peace of mind that your IT assets are thoroughly assessed and protected.
A network security assessment is vital to identify weaknesses in your network that could be exploited by cybercriminals.
It provides insights into your network’s current security posture and recommends necessary enhancements. Trust GoGeekz to deliver a detailed network security assessment that bolsters your defenses.
A risk assessment framework is a structured approach to assessing cyber risks, providing a systematic methodology for identifying, analyzing, and responding to cybersecurity threats.
GoGeekz’s risk assessment framework ensures a complete and methodical evaluation, aligning with industry best practices.